Recognising Scam Patterns and Preventing Data Loss: A Unified Approach
IT Security Guru
NOVEMBER 20, 2023
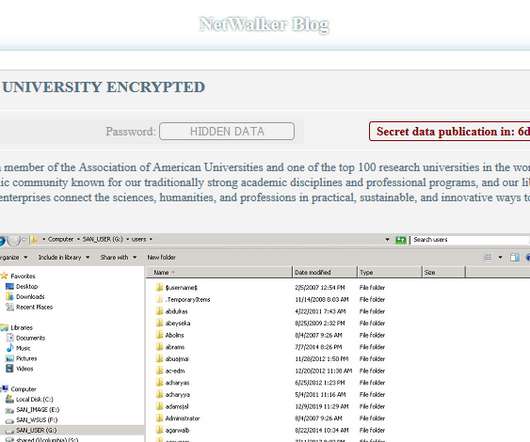
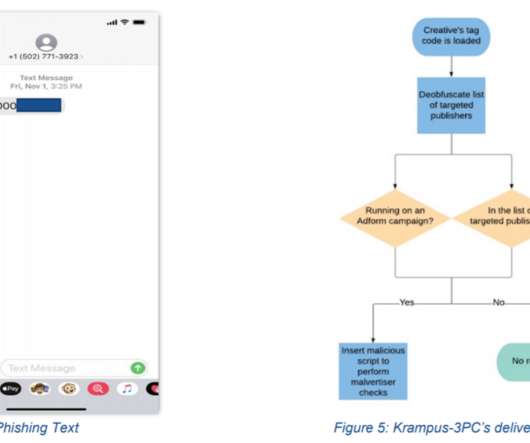
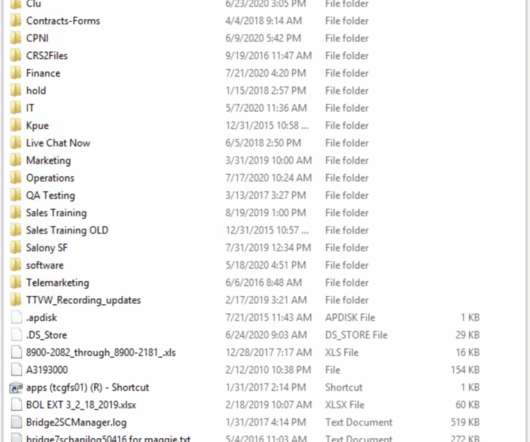
Spear Phishing While phishing remains one of the most prevalent methods cybercriminals use, spear phishing represents a refined form of the traditional phishing technique. Malvertising Malvertising is a tactic where cybercriminals exploit online advertising networks to disseminate malicious advertisements.















































Let's personalize your content