Unmasking Crypto Scams: The Team Effort Behind the Con
Digital Shadows
FEBRUARY 2, 2023
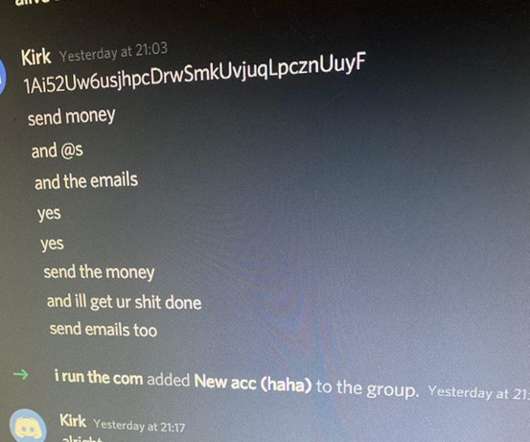
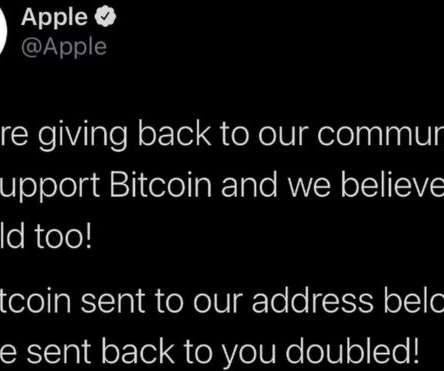
Whether you’re a crypto-skeptic or a crypto-maximalist, it cannot be denied that the mostly unregulated cryptocurrency ecosystem is no stranger to fraud. To conduct attacks specifically linked to cryptocurrency, threat actors must usually cooperate within a web of associates—just like any other area of cyber crime.


























Let's personalize your content