Researchers say enterprise password manager hit in supply chain attack
SC Magazine
APRIL 23, 2021
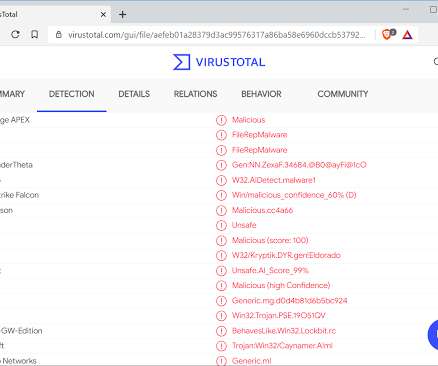
In an April 23 blog , the firm claimed to have digital evidence that Australian company ClickStudios suffered a breach, sometime between April 20 and April 22, which resulted in the attacker dropping a corrupted update to its password manager Passwordstate. ” “At Click Studios we take the privacy of our customers very seriously.




































Let's personalize your content