Aquabot variant v3 targets Mitel SIP phones
Security Affairs
JANUARY 29, 2025
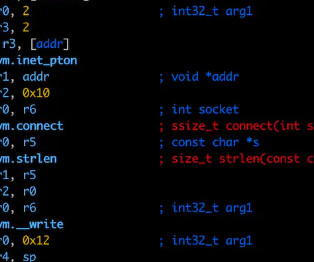
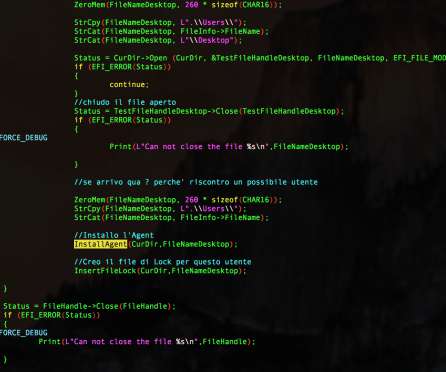
In mid-July 2024, Mitel addressed the vulnerability with the release of firmware updates. “In his GitHub README, Burns reported that he found that the Mitel 6869i SIP phone, firmware version 6.3.0.1020, failed to sanitize user-supplied input properly, and he found multiple endpoints vulnerable to this. HF1 (R6.4.0.136).















































Let's personalize your content