State of Malware 2024: What consumers need to know
Malwarebytes
FEBRUARY 6, 2024
We have seen news of ChatGPT leaking user’s information and law enforcement asking for backdoors in encryption routines. Passwords Google and Microsoft made good on their promise to back passkeys , an encryption-based alternative to passwords that can’t be stolen, guessed, cracked, or phished. This is changing.




















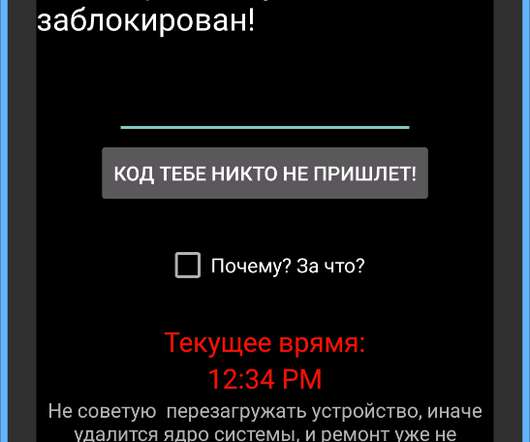






Let's personalize your content