Is your whole digital life protected? 4 ways to address common vulnerabilities
Webroot
FEBRUARY 21, 2025
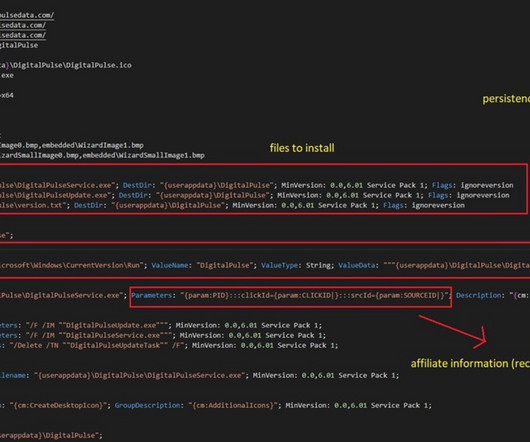
Cyber threats. As more aspects of our lives move online and digital devices proliferate, staying safe from threats has become more important than ever. Effective security software shields you from worms, trojans, adware , and more. Identity theft. Online profiling. Financial fraud. Social media misuse.






























Let's personalize your content