Cyber Threats to the FIFA World Cup Qatar 2022
Digital Shadows
NOVEMBER 10, 2022
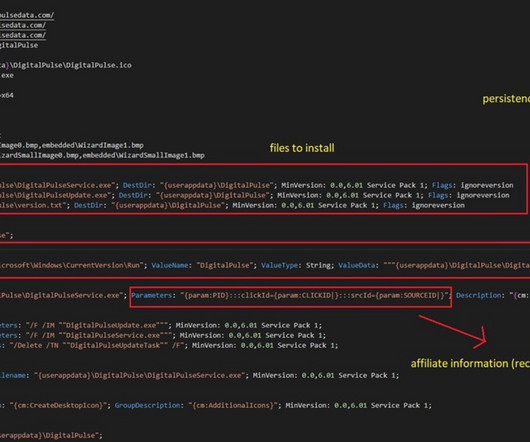
Cyber threat actors, with varying resources and motivations, are highly interested in these eye-catching events too. For instance, financially-motivated threat actors often plant in malicious URLs spoofing these events to fraudulent sites, hoping to maximize their chances of scamming naive internet users for a quick (illicit) profit.























Let's personalize your content