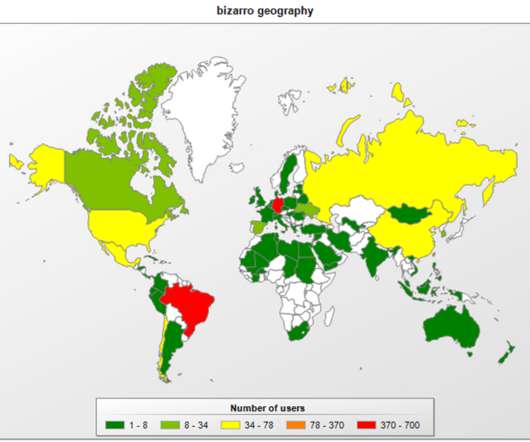
Akira ransomware received $42M in ransom payments from over 250 victims
Security Affairs
APRIL 21, 2024
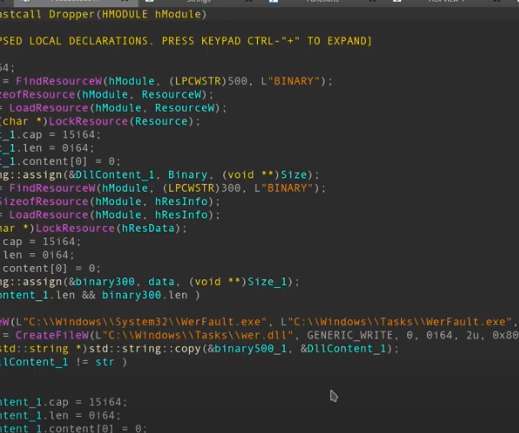
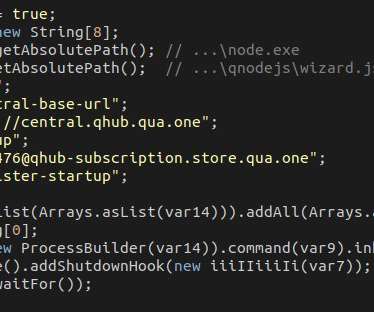
. “ Akira operators have been observed deploying two distinct ransomware variants against different system architectures within the same attack. The operators frequently disable security software to evade detection and for lateral movement. It was this first time that the operators adopted this tactic.














































Let's personalize your content