Hiding Malware in ML Models
Schneier on Security
JULY 27, 2021
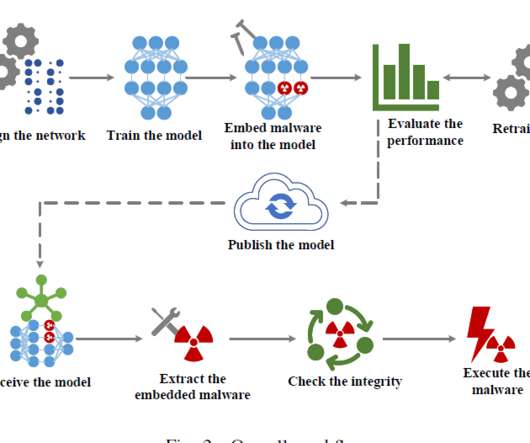
Meanwhile, since the structure of the neural network models remains unchanged, they can pass the security scan of antivirus engines. With the widespread application of artificial intelligence, utilizing neural networks becomes a forwarding trend of malware.



















































Let's personalize your content