Under the Hood: What Artificial Intelligence on the Endpoint Looks Like
Security Boulevard
DECEMBER 6, 2021
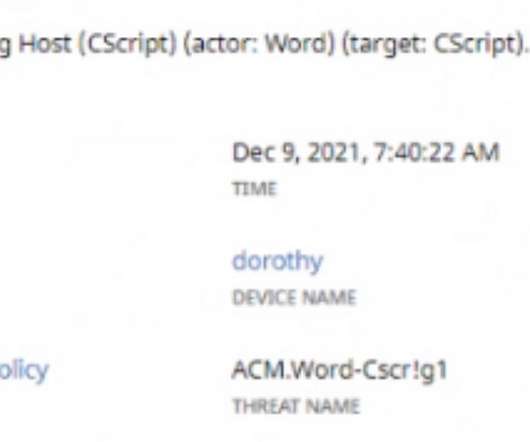
In light of a recent Cybereason research report, Organizations at Risk: Ransomware Attackers Don’t Take Holidays , regarding the prevalence of ransomware attacks that occur during off-hours, it’s imperative that we look towards robust AI security solutions, such that you can know your organization is protected even when none of your staff is online.


















































Let's personalize your content