Scam Information and Event Management
SecureList
OCTOBER 4, 2024
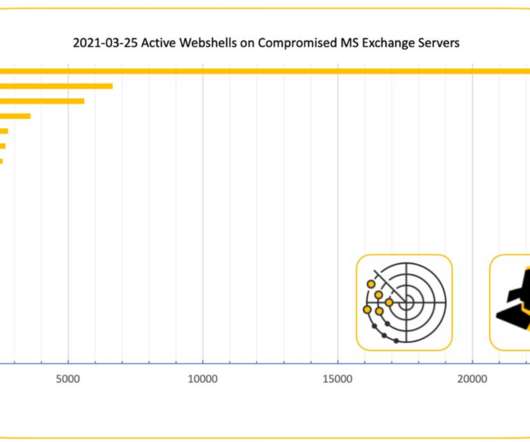
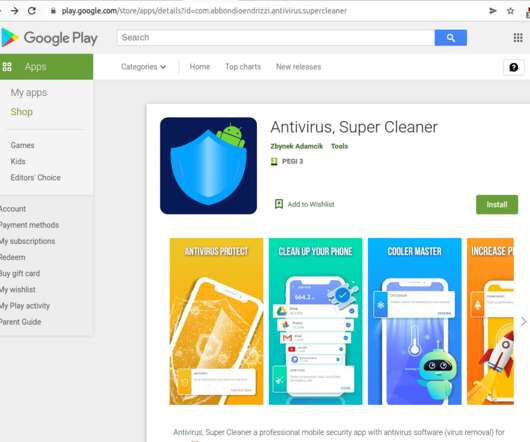
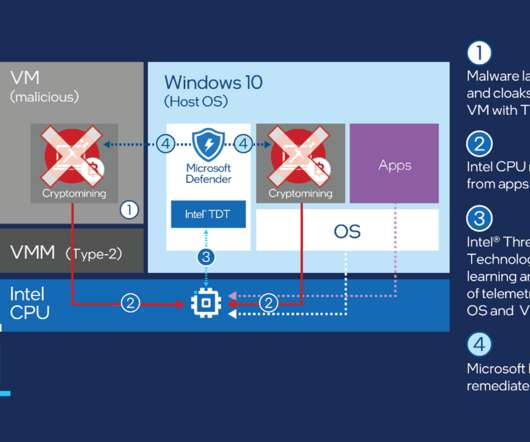
In a recent campaign starting in 2022, unknown malicious actors have been trying to mine cryptocurrency on victims’ devices without user consent; they’ve used large amounts of resources for distribution, but what’s more, used multiple unusual vectors for defense evasion and persistence.








































Let's personalize your content