Fake DDoS protection pages on compromised WordPress sites lead to malware infections
Security Affairs
AUGUST 21, 2022
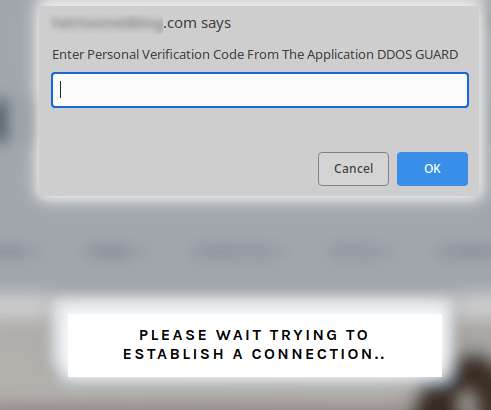
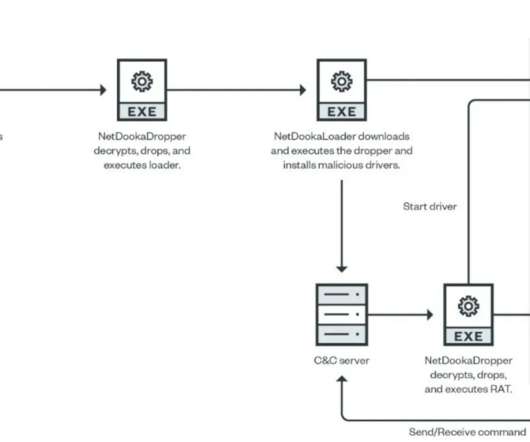
Threat actors compromise WordPress sites to display fake Cloudflare DDoS protection pages to distribute malware. DDoS Protection pages are associated with browser checks performed by WAF/CDN services which verify if the site visitor is a human or a bot. The file poses as a tool required to bypass the DDoS verification.






















Let's personalize your content