Detecting DNS implants: Old kitten, new tricks – A Saitama Case Study
Fox IT
AUGUST 11, 2022
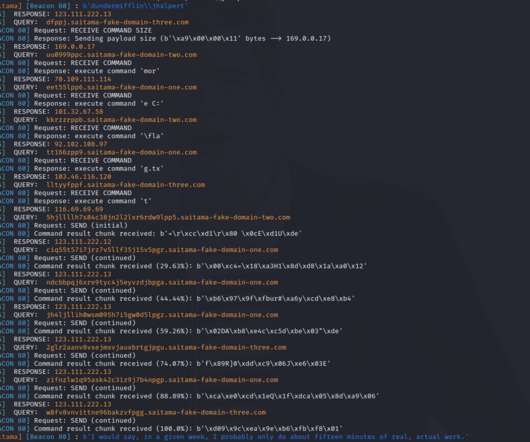
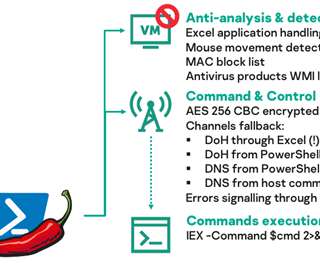
A recently uncovered malware sample dubbed ‘Saitama’ was uncovered by security firm Malwarebytes in a weaponized document, possibly targeted towards the Jordan government. This Saitama implant uses DNS as its sole Command and Control channel and utilizes long sleep times and (sub)domain randomization to evade detection.

































Let's personalize your content