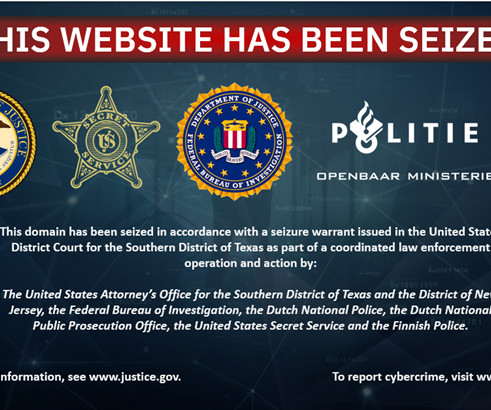
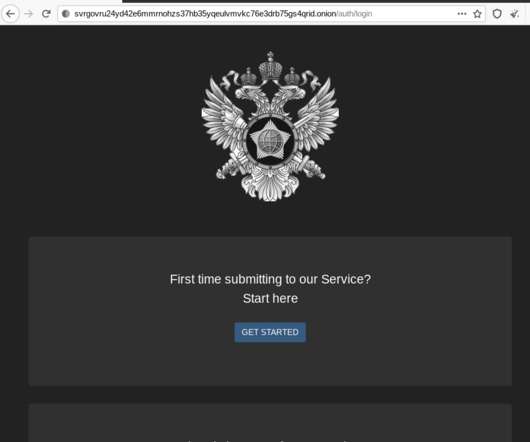
Police took down several popular counter-antivirus (CAV) services, including AvCheck
Security Affairs
JUNE 2, 2025
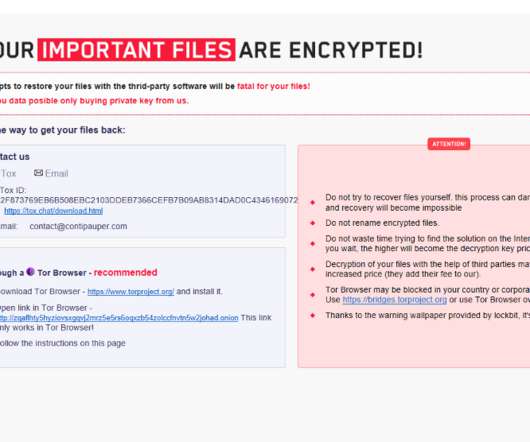
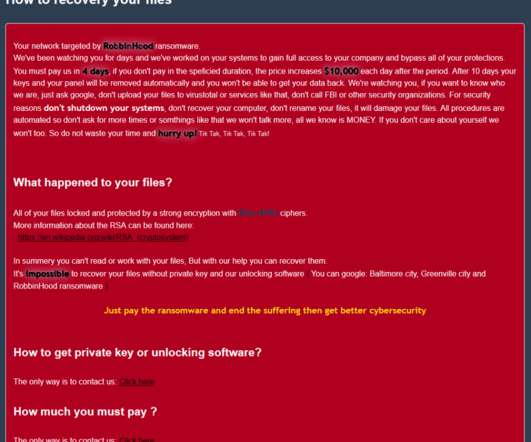
Department of Justice has dismantled an online cybercrime syndicate that provided encryption services to help malware evade detection. “Crypting is the process of using software to make malware difficult for antivirus programs to detect,” the DoJ said. An international law enforcement operation led by the U.S.











































Let's personalize your content