Faults in Our Security: 6 Common Misconceptions in Cybersecurity
SecureWorld News
NOVEMBER 28, 2023
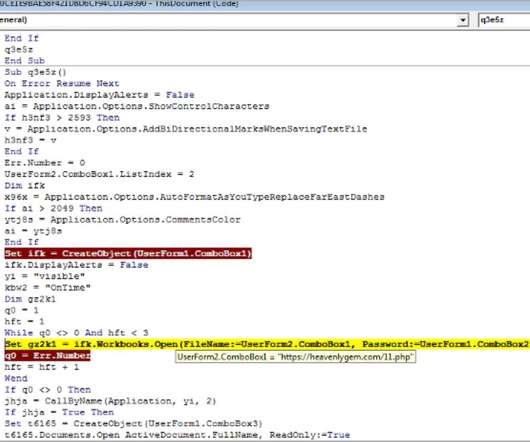
Whether applied to firewall rules or code execution permissions, Default Permit operates on the flawed assumption that allowing everything except known threats is a sound strategy. Relying on exhaustive lists of threats, as seen in antivirus and intrusion detection systems, is impractical.


















































Let's personalize your content