Can Hackers Create Fake Hotspots?
Identity IQ
MARCH 9, 2023
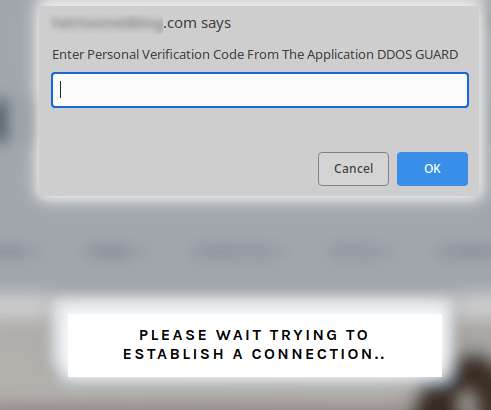
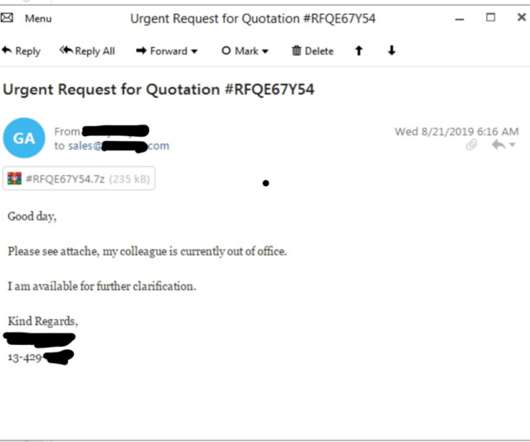
IdentityIQ We rely on the internet, from communicating with loved ones on social media to working and conducting business. The hacker is following the victim’s keystrokes every step of the way, including taking note of any usernames, passwords and financial information the victim is typing. Can Hackers Create Fake Hotspots?














































Let's personalize your content