Hackers take over 1.1 million accounts by trying reused passwords
Malwarebytes
JANUARY 6, 2022
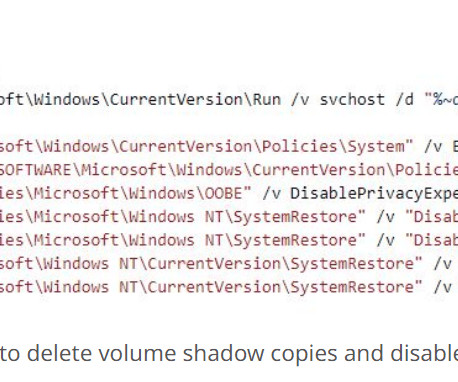
Credential stuffing is the automated injection of stolen username and password pairs in to website login forms, in order to fraudulently gain access to user accounts. Using a forum or social media account to send phishing messages or spam. Start using a password manager. What can users do?













































Let's personalize your content