Malware Evolves to Present New Threats to Developers
Security Boulevard
FEBRUARY 10, 2022
As new forms of malicious code appeared, an antivirus (AV) industry arose to tackle the challenge of detecting and responding to cyber threats. Threat actors quickly realized the shared-responsibility model used by cloud services presented ample opportunities for exploitation. Ransomware. Trojans/Spyware. Logic bombs. a trusted vendor.





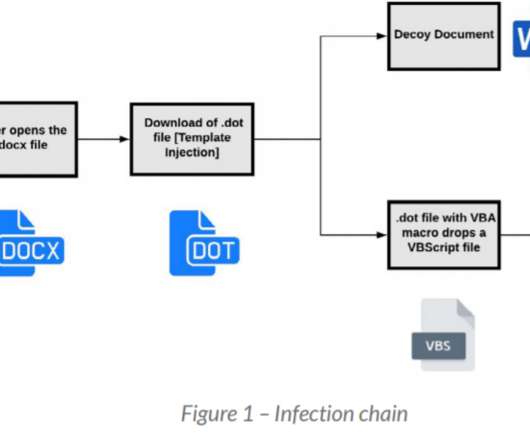








Let's personalize your content