Do You Still Need to Buy Antivirus Software?
Identity IQ
AUGUST 10, 2022
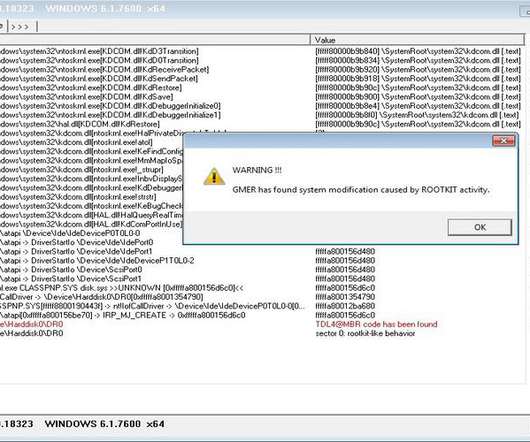
Do You Still Need to Buy Antivirus Software? Technology improvements may mean the “Wild West” days of rampant computer viruses are over, but you still need to take steps to protect your devices. Most modern computer operating systems already have built-in antivirus protections that are consistently updated. IdentityIQ.
















































Let's personalize your content