Thinking of a Cybersecurity Career? Read This
Krebs on Security
JULY 24, 2020
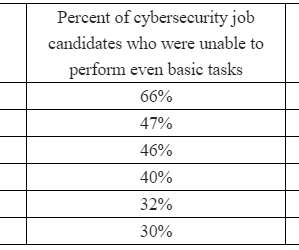
In most cases, the aspirants ask which certifications they should seek, or what specialization in computer security might hold the brightest future. Trying to get a job in security without a deep understanding of how data packets work is a bit like trying to become a chemical engineer without first mastering the periodic table of elements.


















Let's personalize your content