The Hidden Security Risks of Business Applications
Dark Reading
SEPTEMBER 4, 2020
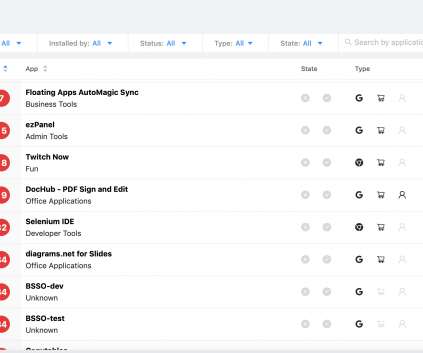
Today's enterprises depend on mission-critical applications to keep them productive, help better serve customers, and keep up with demand. It's important that they also know the risks.


















































Let's personalize your content