Log4j Vulnerability Puts Enterprise Data Lakes and AI at Risk
eSecurity Planet
MAY 18, 2022
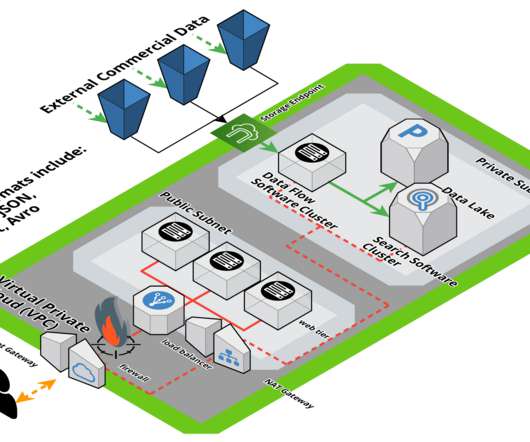
Actually, pretty much all software uses this library written in Java, so it’s a very widespread risk and concern. The infected payload could be injected in Big Data files used to train AI. They tried to use the most realistic processes and cloud architectures to demonstrate the severity of the threat.

















































Let's personalize your content