Software Supply Chain Risks for Low- and No-Code Application Development
Security Boulevard
FEBRUARY 2, 2023
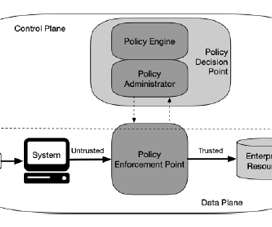
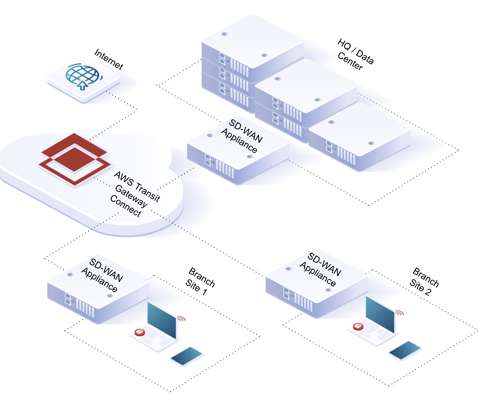
This can happen through backdoors planted in software updates, as seen in incidents like SolarWinds and Kaseya. New architectures such as multi-cloud and microservices have made consistent security controls […] The post Software Supply Chain Risks for Low- and No-Code Application Development appeared first on Radware Blog.












































Let's personalize your content