Left of SIEM? Right of SIEM? Get It Right!
Security Boulevard
JANUARY 12, 2022
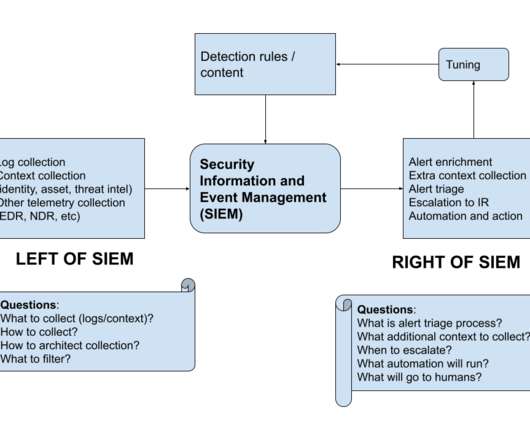
In my opinion, this approach will help make your SIEM operation more effective and will help you avoid some still-not-dead misconceptions about this technology. Mostly data collection. Data collection sounds conceptually simple, but operationally it is still very difficult for many organizations. LEFT OF SIEM.

















Let's personalize your content