Password Storage Using Java
Veracode Security
APRIL 7, 2021
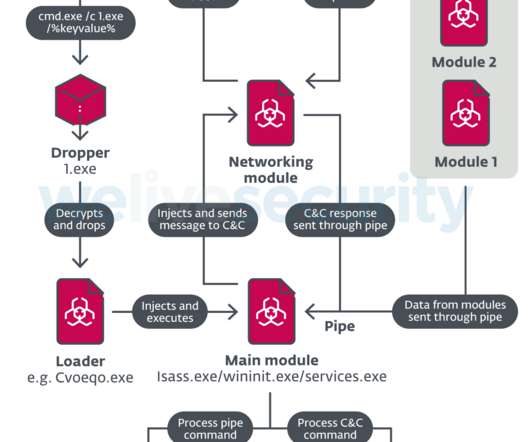
The first few entries talked about architectural details , Cryptographically Secure Random Number Generators , encryption/decryption , and message digests. Password being such a central piece of any authentication-based system, every developer would be involved with it at some point in his or her career. There are two??broad














































Let's personalize your content