The Risk of Stateful Anti-Patterns in Enterprise Internet Architecture
Dark Reading
OCTOBER 17, 2022
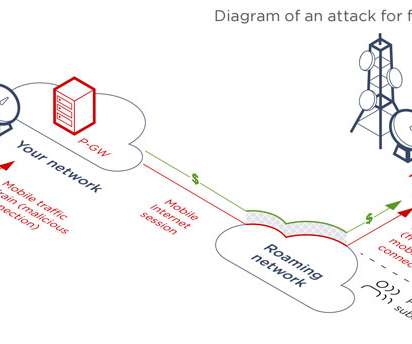
Excessive statefulness hurts the ability to scale networks, applications, and ancillary supporting infrastructure, thus affecting an entire service delivery chain's ability to withstand a DDoS attack.













































Let's personalize your content