QSC Malware Framework: New Tool in CloudComputating Group’s Cyberespionage Arsenal
Penetration Testing
NOVEMBER 10, 2024
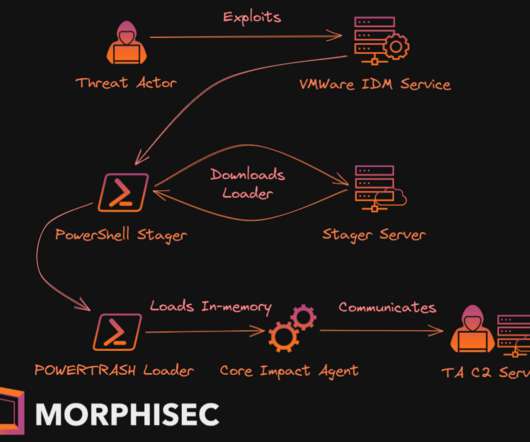
Kaspersky Labs has unveiled an advanced malware framework, QSC, reportedly deployed by the CloudComputating group (also known as BackdoorDiplomacy).

















































Let's personalize your content