News alert: Seraphic launches BrowserTotal™ — a free AI-powered tool to stress test browser security
The Last Watchdog
JUNE 9, 2025
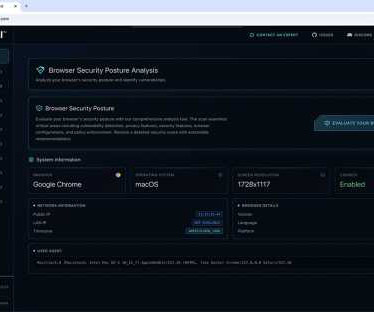
Tel Aviv, Israel, June 9, 2025, CyberNewswire — Seraphic Security , a leader in enterprise browser security, today announced the launch of Browser Total , a unique and proprietary public service enabling enterprises to assess their browser security posture in real-time.


















































Let's personalize your content