U.S. Critical Infrastructure: Addressing Cyber Threats and the Importance of Prevention
The State of Security
MAY 31, 2021
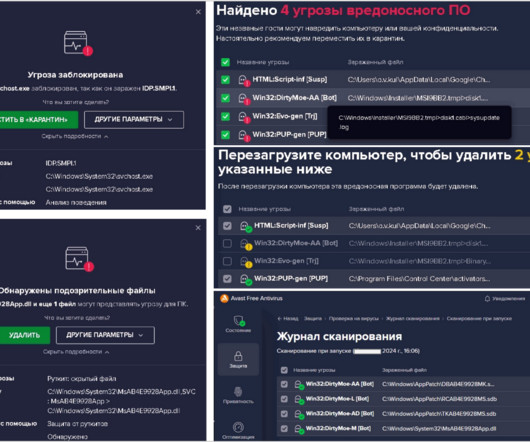
The roads and railways that we travel on; the Internet and the mobile networks that connect us; the water that we drink; the healthcare, financial services and security […]… Read More. Critical Infrastructure: Addressing Cyber Threats and the Importance of Prevention appeared first on The State of Security.












































Let's personalize your content