GUEST ESSAY: The case for leveraging hardware to shore up security — via a co-processor
The Last Watchdog
MARCH 31, 2022
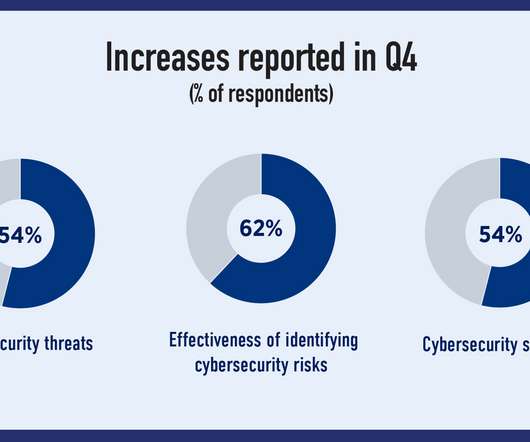
You are no doubt aware of the grim statistics: •The average cost of a data breach rose year-over-year from $3.86 Second, the design of security solutions struggled to scale up properly or adapt to the technological changes in the industry, especially in disaggregated compute networks. Cybersecurity has never felt more porous.


































Let's personalize your content