Cybersecurity in Sports: A New Arena for Risk Management
Centraleyes
MAY 17, 2024
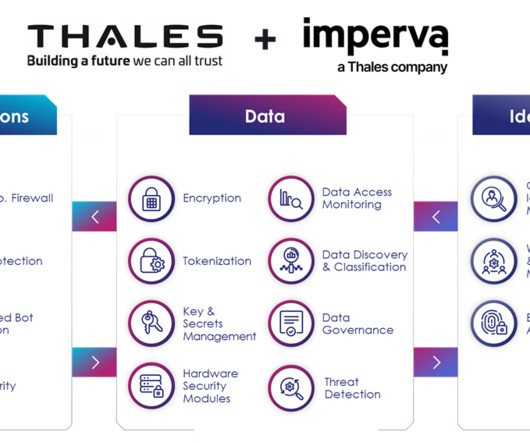
Best Practices To combat these threats, experts recommend: Know Your Data: Identify and protect sensitive information. Secure Vendors: Regularly assess third-party risks. Strong Authentication: Implement multi-factor authentication. Monitor Networks: Use tools to detect suspicious activity.
















































Let's personalize your content