Check Point Warns of Hackers Targeting Its Remote Access VPN
SecureWorld News
MAY 28, 2024
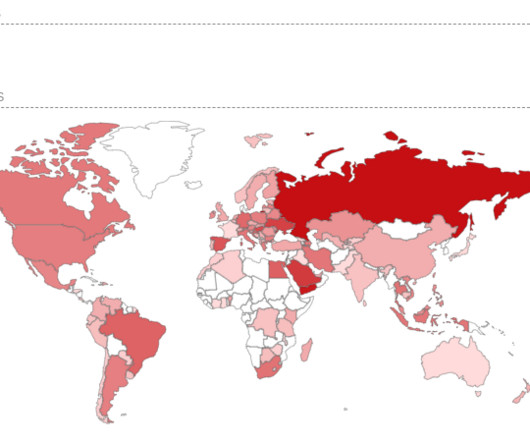
Threat actors are targeting Check Point Remote Access VPN devices in an ongoing campaign to breach enterprise networks, the company has warned in a new advisory. We have recently witnessed compromised VPN solutions, including various cyber security vendors.

















































Let's personalize your content