New GTPDOOR backdoor is designed to target telecom carrier networks
Security Affairs
MARCH 4, 2024
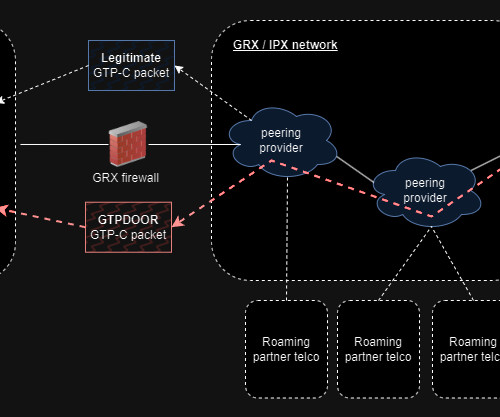
LightBasin targeted and compromised mobile telephone networks around the globe and used specialized tools to access calling records and text messages from telecommunications companies. CrowdStrike researchers reported that at least 13 telecommunication companies were compromised by since 2019.


























Let's personalize your content