Fortnite Scams: What Parents Need to Know
Identity IQ
SEPTEMBER 19, 2023
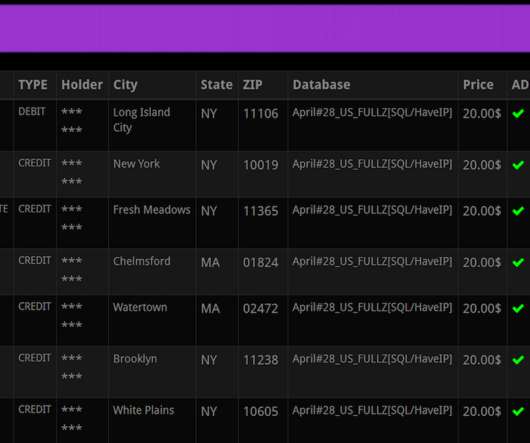
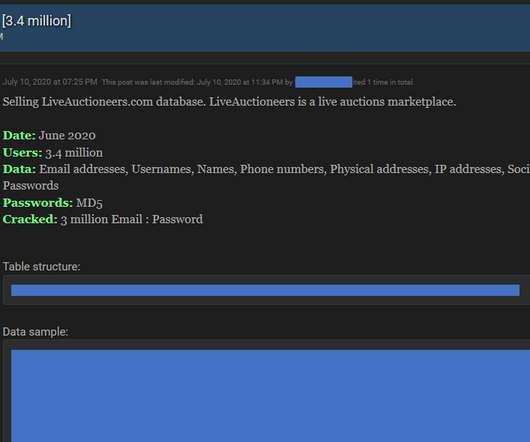
Fortnite Scams: What Parents Need to Know IdentityIQ Since the summer of 2017, Fortnite Battle Royale has been one of the most popular games in the world. Unfortunately, offering financial information exposes players to scams, potentially resulting in identity theft. What is a Fortnite Scam? What is a Poison PDF?







































Let's personalize your content