Failures in Twitter’s Two-Factor Authentication System
Schneier on Security
NOVEMBER 17, 2022
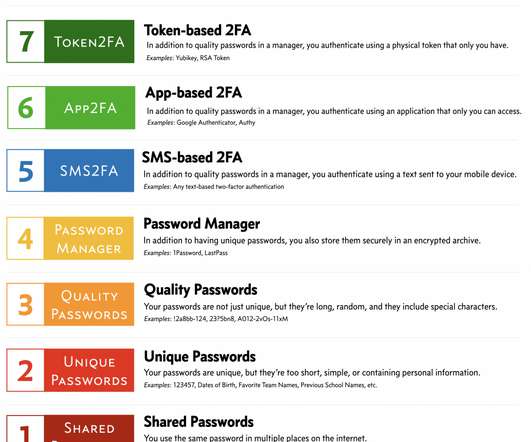
Twitter is having intermittent problems with its two-factor authentication system: Not all users are having problems receiving SMS authentication codes, and those who rely on an authenticator app or physical authentication token to secure their Twitter account may not have reason to test the mechanism.








































Let's personalize your content