A Clear and Present Need: Bolster Your Identity Security with Threat Detection and Response
Duo's Security Blog
NOVEMBER 20, 2023
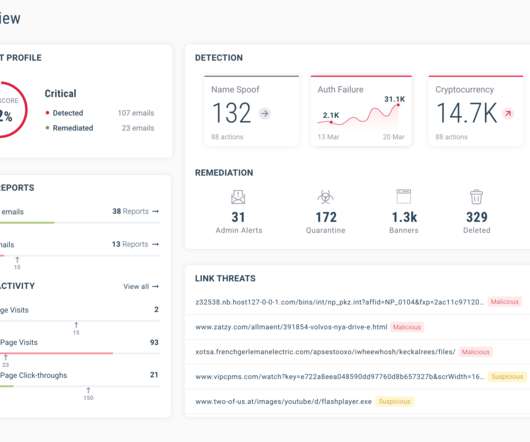
One piece of evidence to support this hypothesis is the low adoption of a basic security control that protects against identity-based attacks - multi-factor authentication (MFA). Add to this, the risks of weak authentication factors such as SMS one-time passcodes and dormant or inactive accounts.
















































Let's personalize your content