Duo’s Data-Driven Defense: Combatting Cyber Threats in Higher Education
Duo's Security Blog
MAY 30, 2024
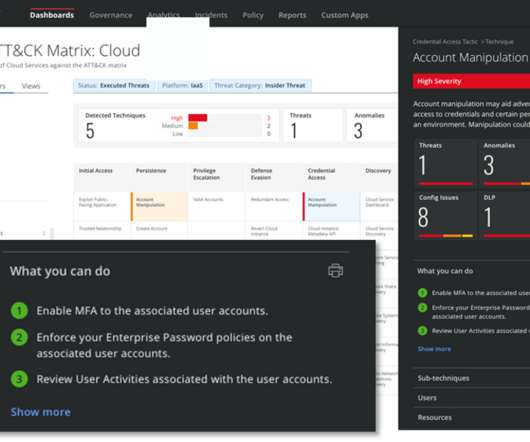
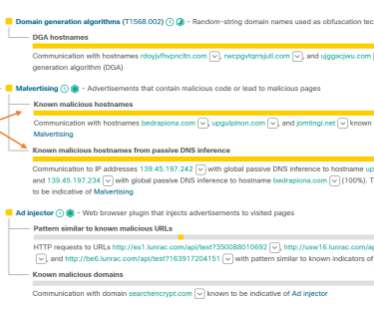
But Duo hasn’t stopped there, as we have a unique ability to respond and establish scalable, structured product enhancements to our threat detection and response capabilities. One device being used to authenticate the account of 27 students across 5 schools? A typical device might be linked to a small number of Duo accounts.

















































Let's personalize your content