Protecting Your Universe from Third-Party Threats with Risk-Based Authentication & Verified Push
Duo's Security Blog
NOVEMBER 14, 2023
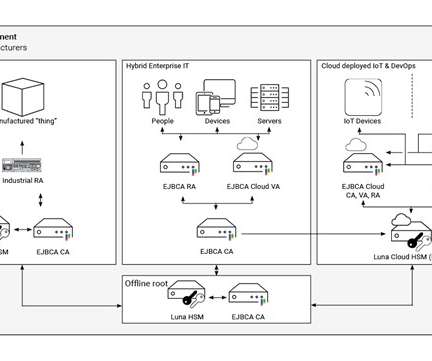
However, the recent spate of software supply chain attacks has heightened awareness amongst security teams and IT on the risks of third parties and how quickly those risks can turn into incidents. In today’s blog, we’ll talk about how RBA and more secure methods of authentication can securely enable third-party access.
















































Let's personalize your content