CISA adds Veritas Backup Exec flaws to its Known Exploited Vulnerabilities catalog
Security Affairs
APRIL 8, 2023
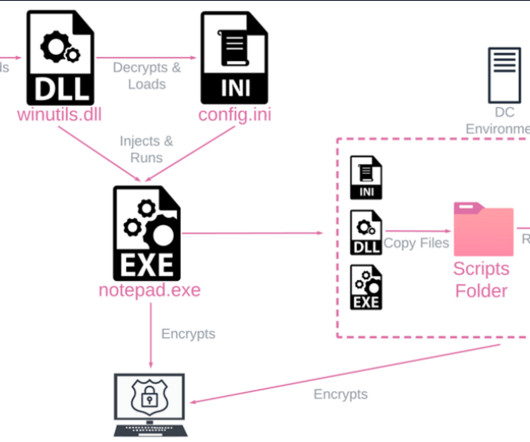
US CISA has added Veritas Backup Exec flaws, which were exploited in ransomware attacks, to its Known Exploited Vulnerabilities catalog. Unlike other ALPHV affiliates, UNC4466 doesn’t rely on stolen credentials for initial access to victim environments.








































Let's personalize your content