“Can you try a game I made?” Fake game sites lead to information stealers
Malwarebytes
JANUARY 3, 2025
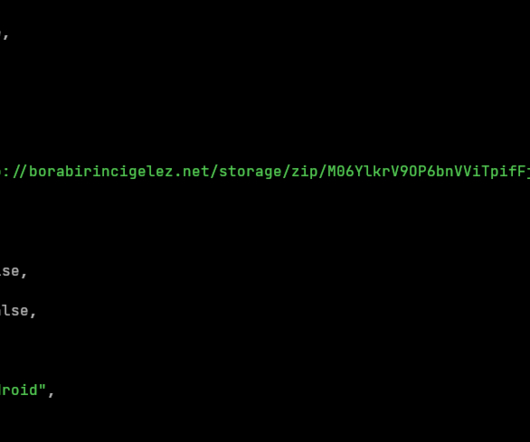
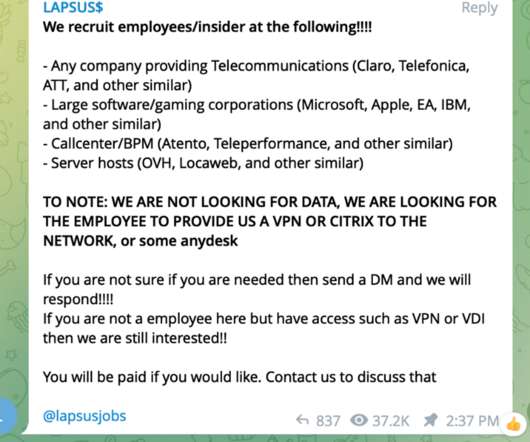
It specializes in stealing credentials stored in most browsers, session cookie theft for platforms like Discord and Steam, and information theft related to cryptocurrency wallets. Part of the Nova Stealers infrastructure is a Discord webhook which allows the criminals to have the server send data to the client whenever a certain event occurs.
















































Let's personalize your content