New EwDoor Botnet is targeting AT&T customers
Security Affairs
NOVEMBER 30, 2021
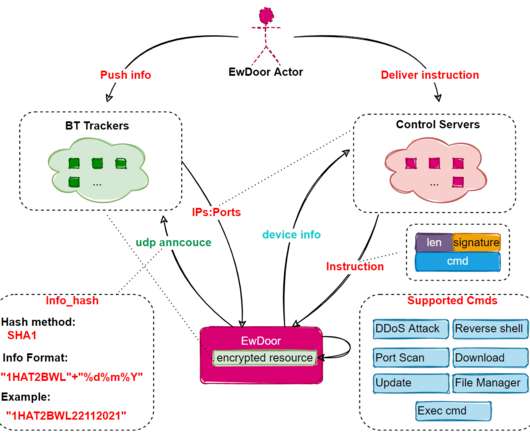
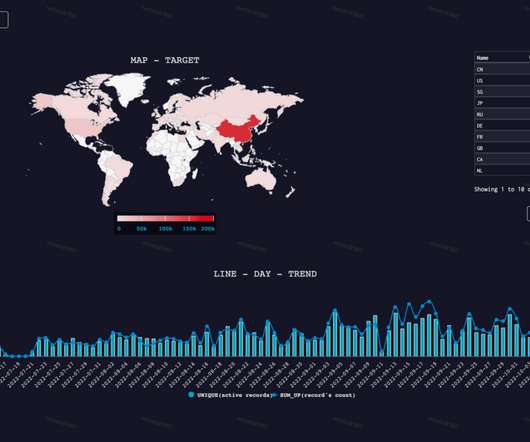
360 Netlab experts spotted a new botnet dubbed EwDoor that infects unpatched AT&T enterprise network edge devices. Researchers have identified 3 versions of the malware, the bot was mainly used to launch DDoS attacks ad to establish a backdoor on infected devices to gather sensitive information, such as call logs.

































Let's personalize your content