Threat actor exploits MS ProxyShell flaws to deploy Babuk ransomware
Security Affairs
NOVEMBER 5, 2021
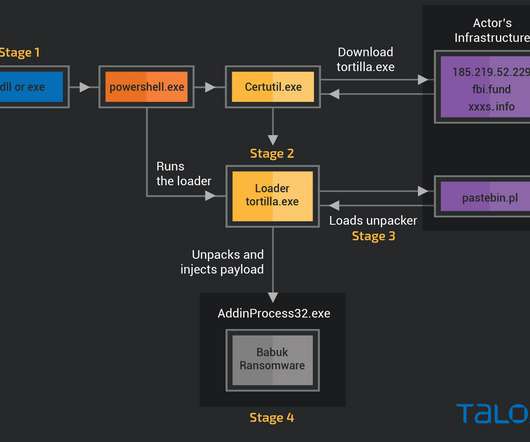
The attack chain starts with a downloader module on a victim’s server in the form of a standalone executable format and a DLL. The DLL downloader is run by the Exchange IIS worker process w3wp.exe. Attackers used a modified EfsPotato exploit to target proxyshell and PetitPotam flaws as an initial downloader.


























Let's personalize your content