Phishing Awareness Training: Best Providers 2020
Spinone
SEPTEMBER 8, 2020
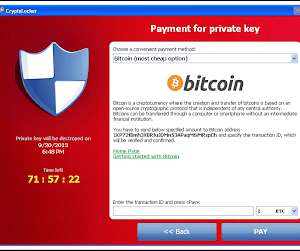
Phishing attacks are one of the main cyber threats involving mistakes by workers. Arranging training for your employees is a great way to protect your company against phishing and its expensive and time-consuming consequences. So, let’s take a look at notable phishing awareness training providers.




































Let's personalize your content