Top Tech Conferences & Events to Add to Your Calendar in 2023
Tech Republic Security
JULY 13, 2023
Looking for a list of the top tech conferences and events in 2023? Explore our guide to find out which events you should add to your calendar.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Tech Republic Security
JULY 13, 2023
Looking for a list of the top tech conferences and events in 2023? Explore our guide to find out which events you should add to your calendar.

Tech Republic Security
JANUARY 23, 2023
The National Cybersecurity Alliance's second annual Data Privacy Week is January 22-28, 2023. Learn how you can participate in virtual events. The post Data Privacy Week 2023: Virtual events and webinars to attend appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Thales Cloud Protection & Licensing
NOVEMBER 19, 2018
The age of Big Data is upon us. And, as more data is available for analytical purposes, more sensitive and private information is at risk. Protecting the confidentiality and integrity and of warehoused data and ensuring that access is controlled is vital to keeping that data secure. respondents.”.

Thales Cloud Protection & Licensing
FEBRUARY 8, 2018
The 2018 Thales Data Threat Report (DTR) has great information on Big Data use and security. We surveyed more than 1,200 senior security executives from around the world, and virtually all (99%) report they plan to use Big Data this year. Top Big Data Security Concerns. Big Data is unstructured.

Security Boulevard
FEBRUARY 3, 2021
The post BSidesSF 2020 – Geller Bedoya’s ‘Serverless Osquery Backend And Big Data Exploration’ appeared first on Security Boulevard. Additionally, the BSidesSF 2021 Conference will take place on March 6 - 9, 2021 - with no cost to participate.

The Last Watchdog
SEPTEMBER 27, 2021
Phishing scams, malware, ransomware and data breaches are just some of the examples of cyberthreats that can devastate business operations and the protection of consumer information. Here are five notable historical events that influenced cybersecurity assessment and transformed it into what it is today: The Battle of Midway (1942).

Security Boulevard
AUGUST 13, 2021
Berta’s ‘The Unbelievable Insecurity Of The Big Data Stack’ appeared first on Security Boulevard. Our thanks to DEFCON for publishing their outstanding DEFCON Conference Main Stage Videos on the groups' YouTube channel. The post DEF CON 29 Main Stage – Sheila A.

CyberSecurity Insiders
OCTOBER 22, 2021
As the industry’s premier global cybersecurity intelligence event, Detect LIVE is where security executives, practitioners, threat analysts, and researchers from all over the world share their insights and expertise on how they use intelligence-driven detection and response to combat surging adversaries. LinkedIn: [link]. Blog: [link].

Spinone
JUNE 8, 2018
While the potential of Big Data is vast, it might lag behind as a standalone tool to deal with hackers due to the enormous volume of data to analyze. There is a huge difference between raw data collected and meaningful insights that can benefit enterprises in their attempt to prevent cyber attacks.

The Last Watchdog
MARCH 19, 2019
Security information and event management, or SIEM, could yet turn out to be the cornerstone technology for securing enterprise networks as digital transformation unfolds. Here are a few takeaways: Very Big Data. Fundamentally, SIEMs collect event log data from internet traffic, as well as corporate hardware and software assets.

Tech Republic Security
APRIL 2, 2024
Discover what industry experts think the events of Q1 mean for the business cyber security landscape in the UK.

CyberSecurity Insiders
MAY 7, 2021
NASDAQ: EVBG), the global leader in critical event management ( CEM ), today announced the completion of its acquisition of xMatters, a leading provider of IT Service Operations, Cybersecurity and DevOps incident response management. BURLINGTON, Mass.–( –( BUSINESS WIRE )– Everbridge , Inc. in the USA and other countries.

Security Boulevard
JUNE 6, 2022
Salt delivers this rich API context through its unique and patented, cloud-scale big data architecture that leverages AI and ML algorithms to gain the most insights into API behaviors. You will find Salt fully represented at all of these important security events. Our latest award comes at a busy time. Attending RSA ?

The Last Watchdog
SEPTEMBER 6, 2019
At the same time, digital transformation has redoubled the complexity of company networks, catapulting us from Big Data to Very Big Data. Consider that 90% of the data that exists in the world was created in two years — 2017 and 2018 — and that our digital universe is on track to swell from 3.2

Security Affairs
JUNE 29, 2019
Attunity data integration and big data management firm exposed a significant amount of sensitive data through unprotected Amazon S3 buckets. Data integration and big data management firm Attunity exposed a significant amount of sensitive data through unprotected Amazon S3 buckets.

Thales Cloud Protection & Licensing
NOVEMBER 3, 2021
One of the first post-pandemic large-scale, in-person events recently took place in Dubai. Some of the enhancements include the implementation of the Thales CipherTrust Data Security platform. Customers were interested in all the portfolios of encryption, MFA, data protection, and access management. Wed, 11/03/2021 - 07:29.

Security Boulevard
DECEMBER 29, 2022
. Russel Ackoff was the one of first to define a hierarchy from data to wisdom (1). In Ackoff’s words: "Data are symbols that represent the properties of objects and events. Information consists of processed data, the processing directed at increasing its usefulness. For example, census takers collect data.
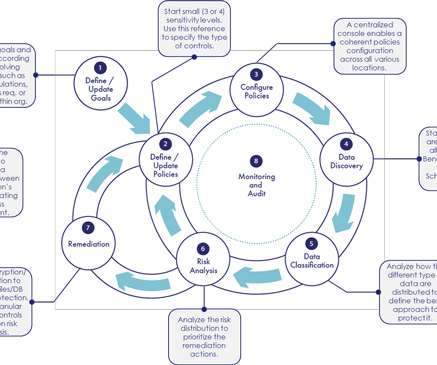
Thales Cloud Protection & Licensing
MARCH 16, 2021
Today, organizations are struggling to control their data environments. The amount of data created is forecasted to grow and be spread in a wide diverse ecosystem: the cloud, on premises, in data lakes and big data. The data visibility process is not a one-time event. The Suggested Path to Follow.

The Last Watchdog
AUGUST 29, 2019
Fortunately, there is a cottage industry of cybersecurity vendors , Exabeam among them, engaged in proactively advancing ways for SOC analysts to extract more timely and actionable threat intelligence from their security information and event management ( SIEM ) and user and entity behavior ( UEBA ) systems.

The Last Watchdog
AUGUST 30, 2021
Security Information and Event Management (SIEM) is not what it was 20 years ago. Querying at scale is a long-recognized challenge of legacy SIEM solutions; when you intentionally create a big data problem, you must also find a way to solve it. Related: The unfolding SIEM renaissance. They also require strategic planning.

CyberSecurity Insiders
NOVEMBER 7, 2022
As a result, security teams are leveraging security capabilities in the form of Security Information and Event Management (SIEM) software to help identify and respond to security threats in real-time. These early SIEMs married both log files (raw data) and security alerts (summarised events).

Security Affairs
MAY 19, 2023
Cookie plugin/WhatsApp plugin/Send plugin : The plugin hooks to Facebook-related apps and intercepts specific activities to launch events. Splash Plugin : Hook popular apps to intercept specific activities such as launching event request ads from advertisements. The plugin also hijacks WhatsApp sessions to send unwanted messages.

Centraleyes
MAY 6, 2024
At the annual InsureTech Connect event in Las Vegas last month, AI won the prize as the most trending topic preoccupying the entire industry. The endorsement expands the definition of a security failure or data breach to include events caused by artificial intelligence. Ready for some more numbers? trillion to $4.4
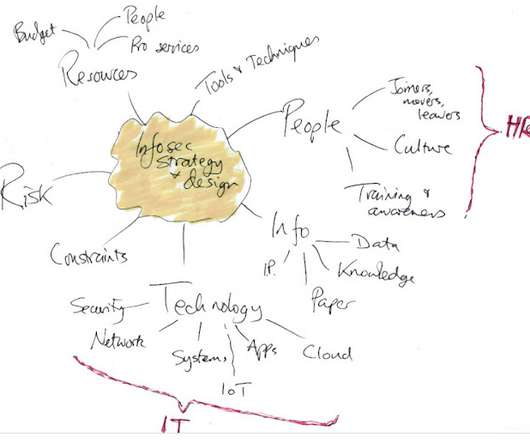
Notice Bored
AUGUST 8, 2022
c omplementing and supporting various other business strategies and architectures such as cloud first, artificial intelligence, IIoT, big data, new products, new markets.); Maintaining a state of 'creative chaos' - meaning a purely reactive event-driven approach - is suboptimal. Bringing clarity and direction (focus!)

CyberSecurity Insiders
DECEMBER 14, 2021
Anomali’s unique innovation focused on the X in XDR to maximize telemetries correlated by intelligence enables customers and partners to detect trillions of events per second,” said Buffo. “I Twitter: [link]. LinkedIn: [link]. Blog: [link]. About Anomali.

CyberSecurity Insiders
JANUARY 6, 2022
The document shares examples, use cases, and treatment methods for how AI, machine learning, and data mining can be effectively utilized throughout a healthcare system, including in research, diagnosis, and treatment.

Thales Cloud Protection & Licensing
OCTOBER 18, 2018
While retailers digitally transform their businesses to better serve the higher demands of their customers, they’re being challenged with safeguarding personal data to protect customers, partners and suppliers’ critical information. Data shows that while more than two-thirds of U.S. The report shows that 95 percent of U.S.

Thales Cloud Protection & Licensing
FEBRUARY 21, 2018
For example, they can use AI to look for unusual security events and find those needles in a haystack faster. So, digital security vendors, such as Cylance and others, are looking at how they can use this powerful tool to more quickly and efficiently solve the data security issues we all wrestle with. AI/ ML is a really good for that.

Security Boulevard
APRIL 27, 2021
In this article, we’ll explain what XDR is, how it relates to traditional security information and event management (SIEM) systems, and how XDR concepts can transform the security organization. The post XDR, SIEM, and the Future SOC appeared first on CCSI. The post XDR, SIEM, and the Future SOC appeared first on Security Boulevard.

SiteLock
AUGUST 27, 2021
The events calender is getting really close to 500,000 active users. Just to know that on average, if I go to a website and I look and they’re using an events calendar, 50% odds it’s ours. To be fair, some of the adoption level and the impact we have on some of our open source plug ins is amazing. That’s kind of amazing.

Security Boulevard
SEPTEMBER 19, 2022
Indeed, no technology can process the large amounts of data needed to accelerate threat detection and response better than AI. The Salt platform uses cloud-scale big data and applies mature, time-tested ML and AI algorithms to provide the context needed to pick out attackers within billions of API calls.

CyberSecurity Insiders
JANUARY 13, 2022
Earlier in his career, he served as Vice President of Worldwide Channels at ArcSight, where he helped to expand the Security Information and Event Management (SIEM) provider’s presence across the global partner and MSSP marketplace. Blog: [link]. Detect LIVE Conference: [link]. About Anomali.

eSecurity Planet
AUGUST 22, 2023
Incident responders and managers alike need training before the event. Know your business, your most important data, the kinds of attacks you might face, and practice the steps you need to limit any network incursions that might turn into big data breaches.

Thales Cloud Protection & Licensing
SEPTEMBER 19, 2019
To start, companies should be open and honest with customers about the security measures that have been implemented to protect their data. For example, in their terms and conditions, assure customers that all their personal data will be tokenized or encrypted so that in the event of a breach, their data will remain protected.

Thales Cloud Protection & Licensing
FEBRUARY 6, 2018
As in previous years, digital transformation remained a key theme at the event as well as discussions around artificial intelligence (AI) and IoT technologies impacting the workforce. There are two opinions out there about these new technologies when it comes to workforce implications.

Thales Cloud Protection & Licensing
JUNE 16, 2022
Identify: An organization must be able to discover data wherever it resides and classify it. This data can be in many forms: files, databases, and big data; spread across storage on-premises, in clouds, and across back-ups. Data security and compliance start with finding exposed sensitive data before hackers and auditors.

Anton on Security
MARCH 16, 2022
User-facing serving systems generally care about availability, latency, and throughput. […] Storage systems often emphasize latency, availability, and durability. […] Big data systems, such as data processing pipelines, tend to care about throughput and end-to-end latency.” This is definitely something I’ve seen in SOCs?—?that

SecureWorld News
JUNE 1, 2021
NIST chemical engineer and co-author of the study, Thomas Cleary, explains it like this: "You lose the data, but you've got the trend up to where the heat detector fails, and you've got other detectors. Using big data to protect firefighters. A tremendous amount of research and testing went into creating P-Flash.

SC Magazine
FEBRUARY 26, 2021
They usually appear in the form of Excel spreadsheets or Word documents with a list of questions posed to a vendor about a potential cybersecurity procurement: Does the product work with big data? Will I need to increase on-site storage for log data? Is the solution compatible with Microsoft 365?

Security Boulevard
APRIL 15, 2022
Production: Turn on logging and monitoring: Telemetry data helps you detect attacks, respond to incidents, and protect APIs in runtime. Use the data as your baseline for normal behavior. That way any outlier events can be quickly identified and resolved.

Spinone
DECEMBER 26, 2018
The Global State of Information Security Survey 2017 suggests that companies should look into deploying threat detection tools and processes (including monitoring and analyzing security intelligence information), conducting vulnerability and threat assessments, penetration tests and security information, and event management (SIEM) tools.

The Last Watchdog
OCTOBER 17, 2023
Combining a security Information tool with a security event tool made it easier to correlate alerts generated by security products, like firewalls and IDS, normalize it, and then analyze it to identify potential risks. We use machine learning models on open choice big data lakes to detect unknown threats early in the attack chain.

Responsible Cyber
NOVEMBER 17, 2021
During the event, several industry thought-leaders will be sharing insights on the importance of connectivity and cybersecurity for I4.0 Those tools empowered by technologies like big data, Internet of things and more require connectivity in some cases, maintenance, and rely mostly on third parties.”
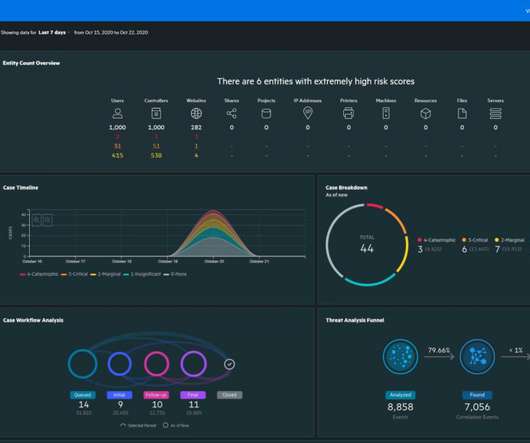
SC Magazine
MARCH 29, 2021
Security information and event management (SIEM) tools are used to collect, aggregate and correlate log data for unified analysis and reporting. While forensic analysis of network events may be a feature of a SIEM, it is not the only feature, nor is it the primary focus of the tool. FINALIST | BEST SIEM SOLUTION.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content