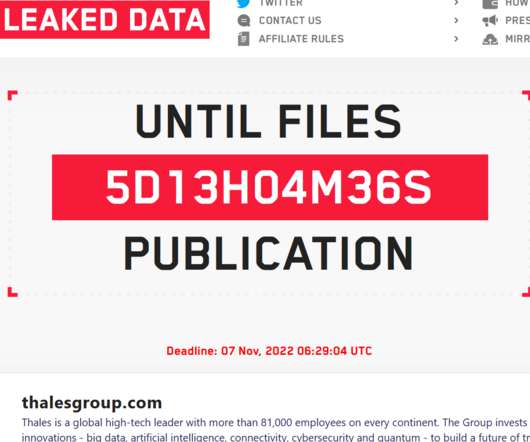
LockBit 3.0 gang claims to have stolen data from Thales
Security Affairs
NOVEMBER 1, 2022
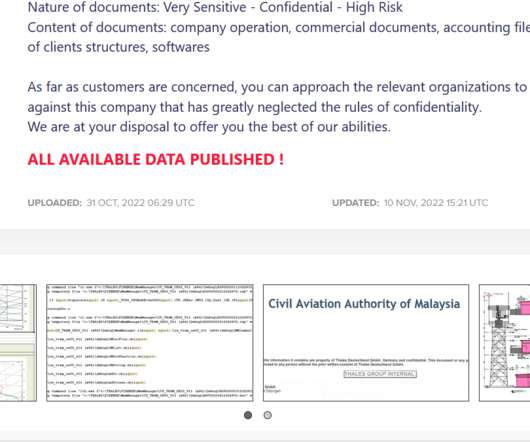
claimed to have stolen data from the French defence and technology group Thales. French defence and technology group Thales confirmed to be aware that the ransomware group LockBit 3.0 claimed to have stolen some of its data. The ransomware group LockBit 3.0 Thales was added to the list of victims of the Lockbit 3.0







































Let's personalize your content